“Teaching computing at Kader isn’t just about coding — it’s about teaching children to think logically, solve problems and understand the digital world they’re growing up in.” Mrs Donkanha

Aims
At Kader Academy, we are committed to providing our students with opportunities to gain knowledge and skills for an ever-evolving digital world. With ICT playing an essential role in both daily life and future careers, our Computing curriculum focuses on digital literacy, computer science, information technology, and online safety. We aim to ensure students become proficient in using technology safely and effectively. Our goal is to inspire a passion for Computing, develop computational thinking, and enhance digital literacy. At Kader, Computing isn’t just about using software but also understanding technology, its societal impact, and fostering creativity and problem-solving skills to prepare students for a digital future.
Approach
Our Computing curriculum ensures progression and breadth across Computer Science, Information Technology, and Digital Literacy, following the National Curriculum.
- Computer Science: Pupils develop computational thinking through coding, algorithms, and problem-solving, using both offline and digital activities.
- Information Technology: They learn to use software, devices, and applications effectively, communicate digitally, and navigate online spaces safely.
- Digital Literacy: Pupils explore responsible technology use, online safety, and the ethical impact of digital interactions.
We integrate Computing into subjects like maths, science, and art, fostering creativity and problem-solving. To support teachers, we provide regular training, workshops, and collaboration opportunities to ensure high-quality Computing education.
This approach equips pupils with essential digital skills, preparing them for the modern world.
Outcomes
The impact of our Computing provision is evident in pupils who confidently and competently use a range of digital tools to solve problems, communicate and create. They show strong computational thinking, applying logical reasoning and coding skills to real-world challenges independently. Our learners are responsible digital citizens, demonstrating a clear understanding of online safety, security and ethical technology use. High levels of engagement and enjoyment are seen in both Computing lessons and cross-curricular projects. Pupils leave well-prepared for the digital world, equipped with the knowledge and skills for further study and future careers in technology. Positive feedback from parents and carers highlights the subject’s role in boosting pupils’ confidence, academic development and safe digital navigation.

Cross-Curricular Links
We actively seek opportunities to integrate Computing across the wider curriculum. Pupils apply their computational thinking skills and digital literacy in subjects such as mathematics, science and art. We encourage creativity, problem-solving and innovation by using Computing as a tool for learning in various subjects.
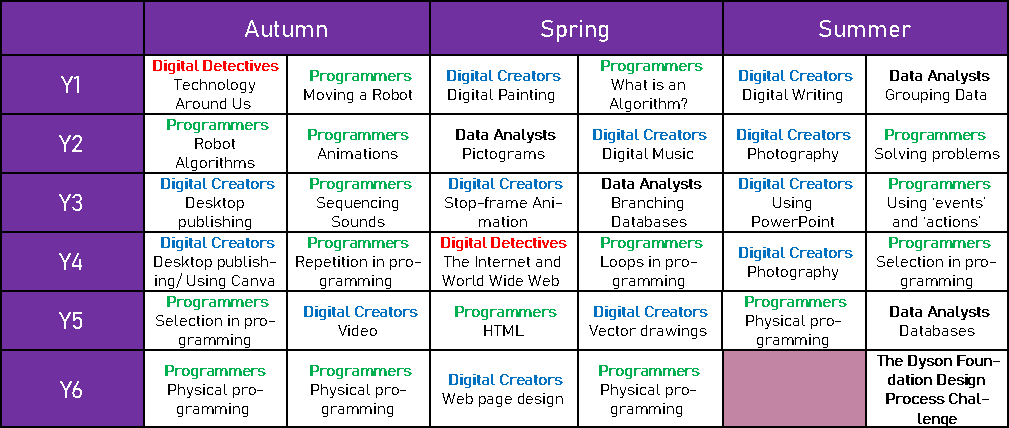
Year group overview (Computing):
Year group overview (Online Safety):
Based on the 8 topics outlined in the UKCIS Education for a Connected World Framework:
Self-image & identity
Online relationships
Online reputation
Online bullying
Managing online information
Health, wellbeing & lifestyle
Privacy & security
Copyright & ownership
Each year group specific lessons based on one of the key themes throughout the year. Online Safety is also woven through the curriculum areas to ensure our children have the knowledge and skills to become responsible digital citizens, with a strong understanding of online safety, security and the ethical use of technology.
Useful links:
Computing:
https://www.barefootcomputing.org/homelearning?ref=blog.teachcomputing.org
https://projects.raspberrypi.org/en/codeclub?ref=blog.teachcomputing.org
https://www.computingatschool.org.uk/homelearning?ref=blog.teachcomputing.org
Online Safety:
https://www.nspcc.org.uk/keeping-children-safe/online-safety
